GOAD Active Directory LAB Setup on a Windows host
In this write-up, I am going to explain how I set up the GOAD Active directory lab from my Windows host using VMware, along with a number of errors and steps and procedure I went through how I fixed them.
GOAD (Game of Active Directory) lab is created by Orange Cyberdefense to provide pentesters a ready-to-use, vulnerable AD environment in which to practise common attack methods.
As described in the Github page, “the lab is intended to be installed from a Linux host”, but it is still possible to successfully install the lab from a Windows host. I did not want to install the lab inside a virtual Ubuntu machine, as nested virtualisation would slow down performance too much.
On high level, my setup will look like:
Windows host: with Vagrant installed to run the VMs on VMware.
VMware Pro: with Ubuntu 22.04 VM installed to run ansible playbooks to make the AD vulnerable.
In this environment, there are two different available labs:
GOAD : 5 vms, 2 forests, 3 domains (full goad lab)
GOAD-Light : 3 vms, 1 forest, 2 domains (smaller goad lab for those with a smaller pc)
I am going to install GOAD-Light with the following VMs:
DC01 — kingslanding
DC02 — winterfell
SRV02 — castelblack
My Setup:
-Vagrant installed
-Type2 Hypervisor > VMWare Workstation Pro
-Ansible setup
-Python3.8.x installed
-Python3,8 virtual environment setup
-Ansible pywinrm installed
High Level Diagram:
-Install Vagrant
https://developer.hashicorp.com/vagrant/install/vmware
Requirements
We will need Vagrant to build all virtual machines I’ve mentioned above. I first started to install Vagrant VMware Utility on my Windows host.
If you do not have VMware, you can use Virtualbox and install Vagrant Virtualbox Utility.
When you successfully complete the Vagrant installation, you can check again whether the installation was successful via powershell or cmd:
-Install Vagrant VMware utility
https://developer.hashicorp.com/vagrant/install/vmware
-Install Vagrant VMware plugin via CommandShell
vagrant plugin install vagrant-vmware-desktop
For the provisioning part, we have 3 ways to follow as they explained in this github page:
You can run ansible from :
a docker container
OR your linux host
OR a linux VM with an host only adapter on the same network as the lab’s vms.
I will follow the third option and use the Ubuntu VM to run the ansible scripts from this VM. I needed to configure the network settings so that all VMs can access each other on the same network. I will show you the network configuration during installation.
I installed Ubuntu 22.04 Desktop on my VMware.
Installing VMs using Vagrant
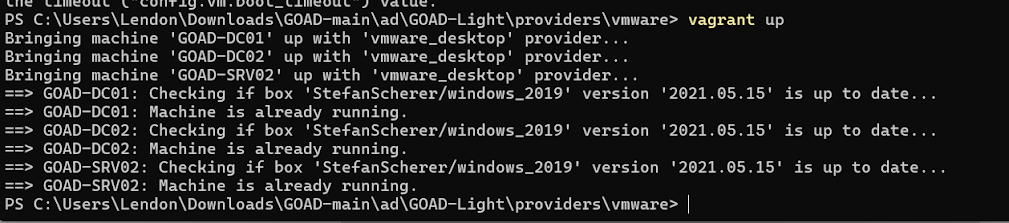
If you downloaded the GOAD project from Github, we can now run vagrant to build VMs.
Run vagrant up on the ..\GOAD-main\ad\GOAD-Light\providers\vmware folder.
In case you want to install GOAD on Virtualbox, remember to change the location accordingly.
-Run provisioning of GOAD VMs thru Vagrant
-Even if they are actually running, you may not see these machines in your VMware Library. You can select “Open all background virtual machines” from the bottom right menu in the toolbar.
Let me first explain how the network configuration should be. We need to have 2 different network adapters:
First network adapter to put 3 VMs and Ubuntu VM on a same host-only network.
Second network adapter to put 3 VMs and Ubuntu VM on a NAT network.
Let’s create the second adapter (NAT) after building all VMs.
For the host-only network, go to: VMware > Edit > Virtual network editor and check the IP address of the host only network. If you don’t have a host-only network, create one.
In my case, VMnet1 is a host only network with 172.16.0.0/24 range.
Since I am going to put all VMs to the VMnet1 network, I am going to give random IPs to 3 VMs from this network:
-Make sure to enable Windows File and Sharing on all VMs to be able to discover and reach each other in the 172.x.x.x network
Now, it’s time to configure the network for all VMs. Go to VM settings of each machine and “Add” a new network adapter under Hardware tab.
Set one network adapter as NAT.
Set the second adapter as custom host-only network to put all on a same virtual private network.
Provisioning
Great! We have created all the virtual machines, now we need to have a vulnerable active directory environment before practicing the attack techniques!
Let’s switch to Ubuntu to start the provisioning part and install all requirements before running ansible.
To install python virtual environment:
-sudo apt install python3-venv
In this case, I encounter some challenges as the version of Python installed comes on my Ubuntu 22.04 OS installation is version 3.10.x.x
I have to install the Python 3.8.x.x to be able to work with the recommended version of Python for the provisioning setup
sudo apt install python3.8 -y
To check the installed version, execute the command python3.8 -V. You should see the following output:
root@host:~# python3.8 -V
Python 3.8.16
Run ansible on your host (or from a linux vm in the same network as the lab)
-If you want to play ansible from your host or a linux vm you should launch the following commands :
-Create a python >= 3.8 virtualenv
sudo apt install git
git clone https://github.com:Orange-Cyberdefense/GOAD.git
cd GOAD/ansible
sudo apt install python3.8-venv
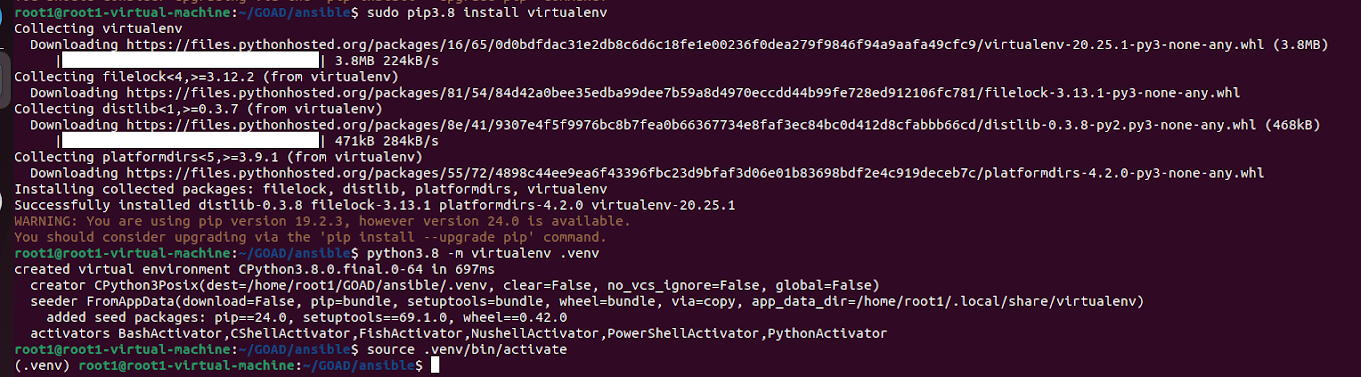
While creating the virtual environment, I encounter another error "No module named virtualenv".
To fix this, I realised I have to run and install the specific module for the python3.8.x version by running the below commands
I then created the virtual environment and activate it
python3.8 -m virtualenv .venv
source .venv/bin/activate
Install ansible and pywinrm in the .venv:
ansible following the extensive guide on their website ansible.
Tested with ansible-core (2.12)
pywinrm be sure you got the pywinrm package installed
python3 -m pip install --upgrade pip
python3 -m pip install ansible-core==2.12.6
python3 -m pip install pywinrm
Install all the ansible-galaxy requirements
-ansible windows
-ansible community.windows
-ansible chocolatey (not needed anymore)
-ansible community.general
ansible-galaxy install -r requirements.yml
Then you can launch the ansible provisioning with (note that the vms must be in a running state, so vagrant up must have been done before that)
We will use the following command to run ansible playbooks for GOAD-Light on VMware provider.
ansible-playbook -i ../ad/GOAD-Light/data/inventory -i ../ad/GOAD-Light/providers/vmware/inventory main.yml # this will configure the vms in order to play ansible when the vms are ready (for vvmware provider and GOAD lab)
However, we encounter an error which says the provisioning server cannot reach the Domain Controller servers and client server. Upon reviewing the error message it shows we have to configure the correct IP addresses of the server/VMs on the GOAD configuration file to rectify the issue.
To correct the configuration, let's modify the "../ad/GOAD-Light/providers/vmware/inventory" file and change the default IP addresses and replace the IPs we’ve set to our VMs.
Now, let's run ansible again to continue provisioning our GOAD environment.
Now, looks like we have another error. :)
The Ubuntu VM can successfully reach DC02, but SRV02 and DC01 seems to be unreachable for some reason. The IP address is correctly assigned to the machines already as we have configured earlier. At this point, I'm already exhausted. :)
The next day, :)
I checked the troubleshooting page of GOAD and found a solution to the issue. I have ensure the IP addresses of the SRV02 and DC01 machine is the current IP addresses which reflects in the configuration file in GOAD config and I have removed the following lines in the ../ad/GOAD-Light/providers/vmware/inventory GOAD file.
Now, let's run ansible again to complete the provisioning of our GOAD environment.
All servers are reachable by Ubuntu now and the ansible playbook is provisioning and setting up the GOAD environment now.
I had run ansible multiple times and Voila! :)
Looks like, all the playbooks were successfully provisioned now!
The purpose of running ansible playbooks (Infrastructure as Code) in this lab is to automate the provisioning of the Domain Controller environment e.g. provision main DC AD configuration, child DC AD configuration things such as install windows features e.g. enable AD domain services, RSAT-ADDS, add child domain to parent domain, etc.
On high level, these are the configuration and setup we had automate by running the Ansible playbook
Main DC AD configuration
-ensure the server is domain controller
-configure dns forwarder
-install active directory
-ensure adminstrator is part of enterprise admins
-ensure administrator is part of domain admins
-create users, OU, groups global, groups domain local, GMSA (Group Managed Service Accounts)
-set users SPN list
Child DC AD configuration
-set configure dns to dc01
-install windows features AD Domain Services, RSAT-ADDS, etc
-add child domain to parent domain
-install active directory
-add dns server zone
-create A record for child domain in parent domain
Other Play Tasks: Active Directory Certificate Services, ACL, IIS, mssql, AD synchronization, vulnerability templates, and so on.
-install ADCS
-install windows features ADCS-cert-authority
-install windows features ADCS-web-enrollment
-install-ADCS-CertificationAuthority-PS
-enable web enrollment
Thanks for reading until this part! I appreciate your time and patience. :)
Our GOAD environment is up and running now. We are ready to use this environment to practice various attack methods for Active Directory.
Stay tuned for the ROAD MAP of this LAB as I follow along the GOAD Project by Orange-CyberDefense
-Password reuse between computer (PTH)
-Spray User = Password
-Password in description
-SMB share anonymous
-SMB not signed
-Responder
-Zerologon
-Windows defender
-ASREPRoast
-Kerberoasting
-AD Acl abuse
-Unconstraint delegation
-Ntlm relay
-Constrained delegation
-Install MSSQL
-MSSQL trusted link
-MSSQL impersonate
-Install IIS
-and many more... :)


















Comments
Post a Comment